
Anker
IT security for banks
Cybercrime has long been a real threat to the financial sector. In order to counter this threat by improving the IT security of banks in particular, the legislator is holding the financial sector, which is particularly at risk, accountable. The industry-specific requirements of the CRITIS sector and the Minimum Requirements for Risk Management (MaRisk) determine this legal framework.
In the following, you will learn from practical use cases how our HiCrypt™ encryption solution and SmartLogon™ smart 2-factor authentication solution can support you in improving IT security at your company.
The solutions can be purchased individually or in attractive packages and are ready for use within a very short time – without any time-consuming conversion of your IT infrastructure.
I’m here for you!
Benjamin Prskawetz
T.I.S.P. Consultant IT Security
Sales & Technical Customer Service
+49 371 815 39-213
bp@digitronic.net
Anker
What you achieve:
In terms of data encryption and secure logon to the operating system as well as specialist applications:
- Implementation of the Minimum Requirements for Risk Management (MaRisk)
- Fulfillment of banking supervisory requirements for IT (BAIT)
- Securing the industry-specific requirements for KRITIS sectors
For whom is the application useful?
Financial Services Institutions
Credit institutions
Use Case 1: MaRisk
It must be possible to assign non-personalized authorizations to an acting person without any doubt at any time (preferably in an automated manner). Deviations in justified exceptional cases and the resulting risks must be approved and documented. HiCrypt™ Enterprise Services enables convenient single sign-on to encrypted shares of authorized persons or groups of persons as well as documentation of events.
Use Case 2: Brewer-Nash-Modell
Banks as well as service providers of banks are obliged to create secure and well-manageable data rooms to which only selected personnel have access. With HiCrypt™, you reliably protect your data by storing it on encrypted network drives and protecting it with individual access concepts based on the Brewer-Nash model (also known as the Chinese Wall model) – regardless of your IT administration.
Anker
Need to act fast to secure your employees’ home offices?
If you need to secure your employees’ home offices quickly, for example, our “Get Ready Option” guarantees that we will develop and implement the desired standard product within just 15 working days.
Use Case 3: Need-to-know-Principle
To maintain separation of functions and avoid conflicts of interest between personnel, use HiCrypt™ Enterprise Services to easily implement AD authorization concepts in your digital vaults. The principle of economy is a pillar on which HiCrypt™ Enterprise Services is built.
Use Case 4: BaFin
The German Federal Financial Supervisory Authority (BaFin) audits banks to ensure that IT security measures have been implemented and complied with. Our solutions held up hundreds of times in ISO 27001 certification processes and were accepted by auditors.
Use Case 5: Social Engineering
Not only is the threat from the outside real, but attacks on your employees’ identities or the theft of their passwords are also serious threats. Protect yourself and your employees with advanced authentication using SmartLogon™ and training from our expert IT security consultants at your facility or virtually.
Use Case 6: Confidentiality
All IT systems, IT processes and other components of the information network must ensure IT security. This means that the integrity, availability, authenticity and confidentiality of data must be ensured at all times. Data encryption with HiCrypt™ reliably maintains the confidentiality of sensitive information.
Our promise as a manufacturer
As a manufacturer and long-standing IT security expert, we are happy to work with you to develop customizations that best meet your specific requirements.
Software and Support „Made in Germany“
Software and support “Made in Germany” guarantee you: No backdoor access to your confidential data and shortest response times when you need our support.
Use existing technology
Existing transponders or smart cards can usually be used to implement 2-factor authentication. We are happy to check existing hardware for compatibility in order to avoid new purchases.


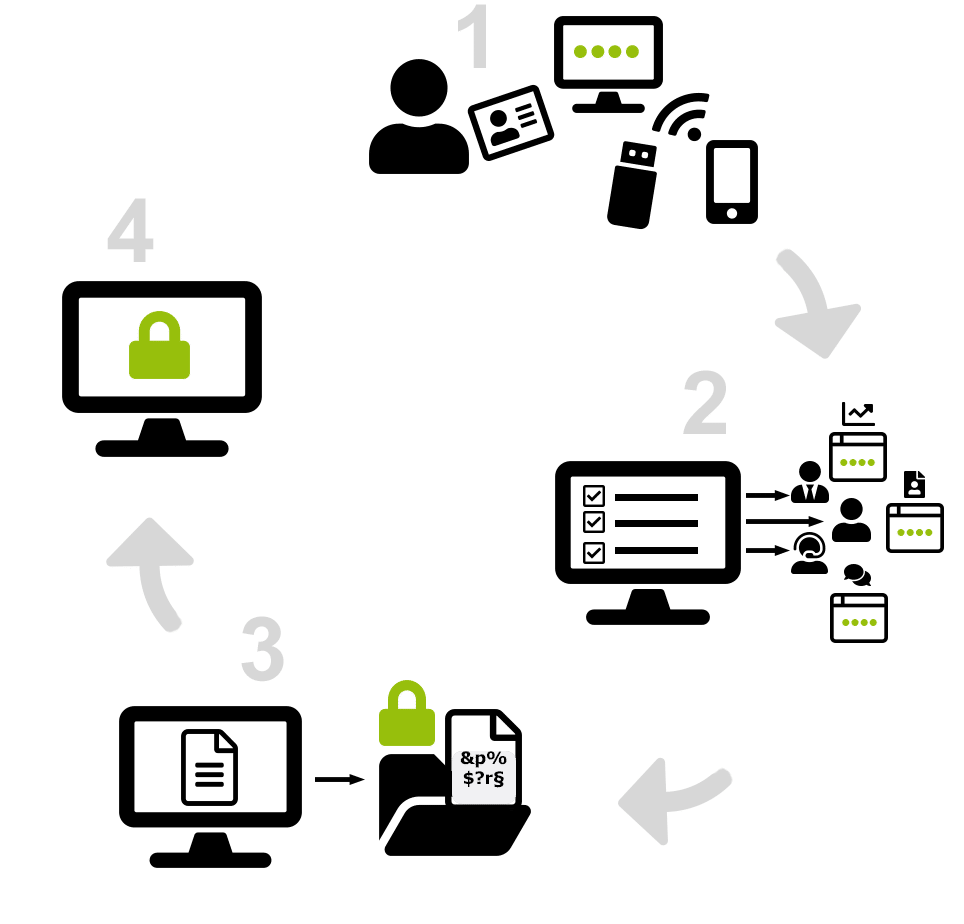
Example scenario 2-factor authentication and data encryption in everyday practice:
1
The PC logon takes place by means of an authentication feature (token) and a short PIN. Smartcards, USB or Bluetooth tokens and even smartphones are suitable as tokens.
2
All logins can be logged and assigned to the respective user profile. If desired, individual specialist applications can be opened according to the profile.
3
Depending on the rights assigned, encrypted files can be viewed or edited in plain text and saved encrypted again. Unauthorized persons only get to see a cryptographic collection of data.
4
Automatic logoff from the operating system, specialized applications, and encrypted files occurs when the token is removed or the user leaves the device.
For digital freedom without risk!
Anker
Our sales and support team will be happy to advise you on our IT security solutions for protecting your confidential customer and financial data. Simply contact us or arrange a presentation appointment.
Make a request now:
Get advice now:

Benjamin Prskawetz
T.I.S.P. Consultant IT Security
Sales & Technical Customer Service

