Chemnitz, 20.07.2021
Reliable data encryption is more important today than ever before. Especially when teams have to work on highly confidential data in a decentralized manner or across national borders. The increasing outsourcing of work to the home office also makes a rethink of the security structure in companies quite sensible.
In the following, we will look at what is actually meant by confidential data, why simple password protection for confidential files and folders is not enough, what the disadvantages of data encryption with Windows on-board tools are, and what alternatives there are to Windows tools.
What is confidential data anyway?
Basically, confidential data is any information that requires special protection and should not fall into the wrong hands. Here it is important for companies to consider two main aspects: The legal and the economic aspect. From a legal perspective, since the enforcement of the General Data Protection Regulation (GDPR), all personal data is particularly worthy of protection. This means that all employee and customer data must be protected from misuse by law, otherwise there is a risk of high financial penalties.
In purely economic terms, however, there is a great deal of other data that requires special protection because it secures a competitive advantage for the company or contains sensitive company internals, such as:
- Research and development data
- Prototype data
- construction plans
- strategic documents
- Project data
- Calculations
- transaction data
- protocols
- memos
- and much more
If confidential information is not adequately protected, in the worst case scenario it can be tapped by hackers – or just as bad, by unauthorized people internally – and fall into the wrong hands.
Password protection for files and folders not secure enough and there is a risk of data loss
- Mostly all documents are protected with one and the same password
- If the password is too simple, it can be easily hacked
- If the password is too complicated, it can be quickly forgotten and you can no longer open the file
Data encryption with Windows on-board tools not consistent enough
Windows therefore brings yet another way to protect sensitive
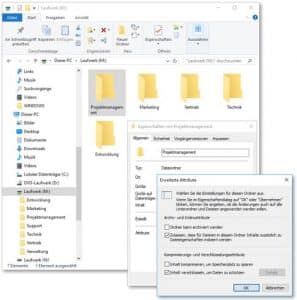
By right-clicking on the corresponding file/folder, you can access the “Attributes” area in the “General” tab via the properties and select the desired compression and encryption attributes there by clicking on the “Advanced” button.
Unfortunately, however, even this variant of data encryption is not consistent enough and bears the risk of data loss, because:
- The generated key is attached to the account ID of your Windows user account, i.e. the file is encrypted only if you open it from another user account
- If a hacker (or an unauthorized employee) logs in with your user account, he sees the file in plain text
- When deleting the user account, the access to the protected files is irrevocably lost, if you have not exported the certificate first
Additional tool for the production of confidentiality
That’s why you can’t avoid using additional tools to adequately protect sensitive information. With the HiCrypt™ encryption solution, for example, you can ensure that only a selected group of people has access to certain data – and that is decoupled from the Windows user profiles. In doing so, HiCrypt™ fully integrates with your familiar Explorer view and runs as an additional network drive alongside your existing ones. By storing data in the HiCrypt™ network drive, the data is automatically encrypted. Access to the protected files is possible from anywhere and in a team. Authorization to view file contents is individually configurable and centrally manageable. Absolutely unique is the clear separation of powers in HiCrypt™ through decoupled access rights. This means that administrators can prepare the drives for encryption, but have no authorization to view the data. This protects them in case of suspicion.

The software is installed in just a few minutes and runs silently in the background. HiCrypt™ is available in the versions “Professional” and “Enterprise Services”. Try HiCrypt™ Professional conveniently for 30 days free of charge or download the fact sheet with further technical information.